Security at Zoom
See why millions of people and organizations trust us with their communications.
More ResourcesProtecting your meetings
Zoom offers several tools to protect your meetings, helping manage participant activity, information sharing, and more.
Protecting your data
Communications are established using 256-bit TLS encryption and all shared content can be encrypted using AES-256 encryption, and optional end-to-end encryption.
Protecting your privacy
Zoom is committed to protecting your privacy. We've designed policies and controls to safeguard the collection, use, and disclosure of your information.
Protecting your meetings
The following in-meeting security capabilities are available to the meeting host:
- Secure a meeting with encryption
- Create Waiting Rooms for attendees
- Require host to be present before meeting starts
- Expel a participant or all participants
- Lock a meeting
- Screen share watermarks
- Audio signatures
- Enable/disable a participant or all participants to record
- Temporary pause screen-sharing when a new window is opened
- Use a passcode to protect a meeting
- Only allow individuals with a given e-mail domain to join
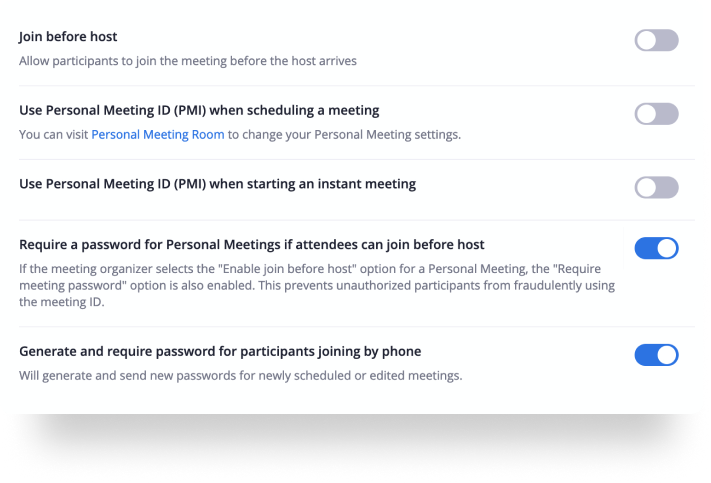
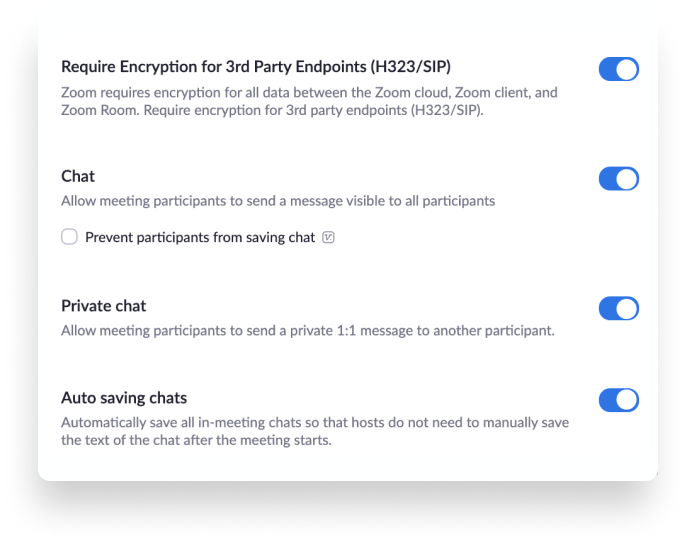
Protecting your data
Chat encryption allows for a secured communication where only the intended recipient can read the secured message. Zoom uses both asymmetric and symmetric algorithms to encrypt the chat session. Session keys are generated with a device-unique hardware ID to avoid data being read from other devices. This ensures that the session can not be eavesdropped on or tampered with.
End-to-end encryption , when enabled, ensures that communication between all meeting participants in a given meeting is encrypted using cryptographic keys known only to the devices of those participants. This ensures that no third party — including Zoom — has access to the meeting’s private keys.
Recordings can be stored on the host’s local device with the local recording option or on Zoom’s cloud with the Cloud Recording option (available to paying customers).
- Recordings stored locally on the host’s device can be encrypted if desired using various free or commercially available tools.
- Cloud Recordings are processed and stored in Zoom’s cloud after the meeting has ended; these recordings can be passcode protected or available only to people in your organization.
- The recordings are stored in both video/audio format and audio only format.
- If a meeting host enables cloud recording and audio transcripts, both will be stored encrypted. If a meeting host enables file transfer through in-meeting chat, those shared files will be stored encrypted as well.
- The meeting host can manage their recordings through the secured web interface.
- Recordings can be downloaded, shared, or deleted.
Zoom Phone Voicemail recordings are processed and stored in Zoom’s cloud and can be managed through the secured Zoom client.
Protecting your privacy
Zoom only stores basic information under user account profile information:
- Email address
- User password - salted, hashed
- First name
- Last name
- Company name (optional to provide)
- Company phone number (optional to provide)
- Profile picture (optional to provide)
For more information about our privacy policy, visit https://zoom.us/privacy.
Authentication methods
Zoom offers a range of authentication methods such as SAML, OAuth, and/or Password-based, which can be individually enabled/disabled for an account. Users authenticating with username and password can also enable Two-Factor Authentication (2FA) as an additional layer of security to sign in.
Zoom works with Okta as well as other enterprise identity management platforms such as Centrify, Microsoft Active Directory, Gluu, OneLogin, PingOne, Shibboleth, and many others. Zoom can map attributes to provision a user to a different group with feature controls.
OAuth-based provisioning works with Google or Facebook OAuth for instant provisioning. Zoom also offers an API call to pre-provision users from any database backend.
Additionally, your organization or university can add users to your account automatically with managed domains. Once your managed domain application is approved, all existing and new users with your email address domain will be added to your account.
Zoom and the EU General Data Protection Regulation (GDPR)
Zoom is committed to helping our users understand the rights and obligations under the General Data Protection Regulation (GDPR), which took effect on May 25, 2018.
We have introduced tools and processes to ensure our compliance with requirements imposed by the GDPR and to help our customers comply as well.
To learn more about our GDPR compliance, please read our GDPR notice.
Enables HIPAA, PIPEDA & PHIPA Compliance
Zoom’s solution and security architecture provides encryption and meeting access controls so data in transit cannot be intercepted.
Zoom does not have access to identifiable health information and we protect and encrypt all audio, video, and screen sharing data.
Healthcare organizations should contact our sales teams to learn more about our solutions and how they can be configured to comply.


